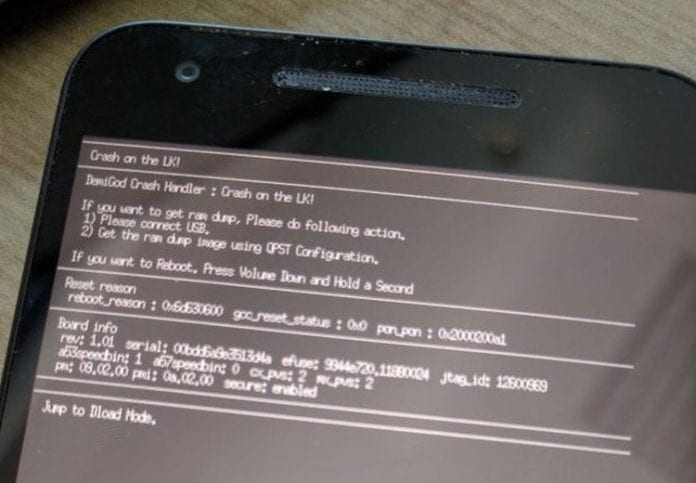
A bug which has been affecting the Nexus 5X phones has been taken care of by Google. The bug was patched by Google and it could expose information which was stored on users handsets even if the phones themselves were password protected.
IBMs X-Force security team was the one which managed to report the security flaw. The team noted that attackers could use the flaw to obtain full memory dumps from the phone. They would use a command line tool that has been used for PCs and one developers have used with USB connected Android devices. The tool is called the Android DeBug Bridge. The bug was reported to affect the older devices, and the researchers said that the exploit was pretty straightforward to use and came about because of a flaw in the fastboot USB interface.
The security team also noted that the flaw could allow attackers to get information and a memory dump from the Nexus 5X, which would mean sensitive information is always bound to be taken by the attackers even if the phone was locked. Hackers could also infect the ADB with a malware if they did not have physical access to the device of the victim.
Another alternative approach if they wanted access to the device would be to plug the handset into a malicious charger. Such kinds of methods would however only be successful in cases whereby the user has had ADB activated on their phones. The target also has to authorize the charger when it connects for it to work.
When the attacker reboots the phone into a fastboot mode, the option can be done without any authentication required. Physical attackers can use the volume down button during the device reboot to activate the fastboot. Attackers in possession of the ADB can also execute this action by simply issuing a command, (adb reboot bootloader). The fastboot mode is therefore exposing the USB interface, which in its case would therefore allow the attacker to command a crash on the bootloader. In the small vulnerable cases of the bootloader the crash then exposes connections which would enable attackers to get memory dumps of the device.
IBM also noted that through the memory dumps, attackers would be able to gain some information such as passwords and other sensitive information which means more attacks in the future.