There are some concepts you pick up by osmosis in the IT world. For instance, if you’re around some IT professionals for long enough, and they start talking shop, it’s more than likely the PKI concept might come up. PKI stands for public key infrastructure.
If you don’t work in IT, you might know nothing about PKI or why it matters. That’s what we’ll talk about right now. We’ll discuss PKI, and also why companies need to know all about it in 2024 and beyond.
What Precisely is PKI?
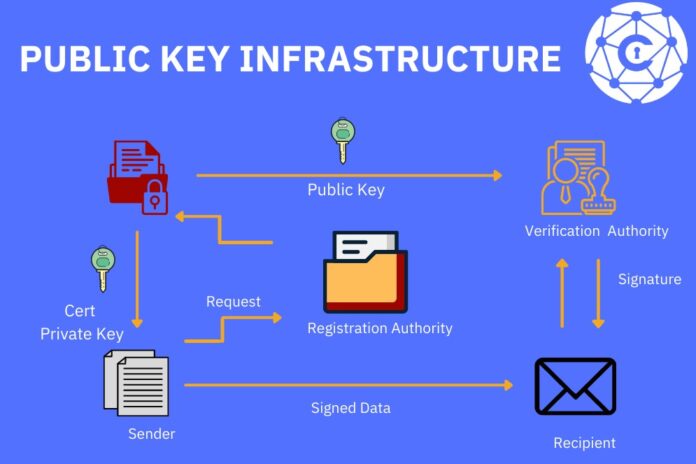
When talking about this concept, JumpCloud says “the role of PKI is evolving.” They’re right about that. Public key infrastructure means a strict set of policies, hardware, roles, procedures, and software. You need these to create, use, distribute, manage, revoke, or store digital certificates.
Digital certificates matter a great deal. This category might include client certificates, SSL certificates, or TLS certificates.
A client certificate assures a server that it is communicating with a legit entity. If you have a client certificate in place, you can ensure that you’re communicating with a valid client and not an imposter. If you’re using email or a website, you’ll want to know that this client certificate is in place.
An SSL certificate is another kind of digital certificate. It verifies a site’s identity and protects a secure connection. SSL stands for secure sockets layer. TSL stands for transport layer security. It’s very similar to SSL.
All of this might sound a little bewildering if you’re not a tech person, so let’s put it another way. PKI exists for security. It’s a system virtually all companies or individuals want to have in place so they can deal with digital certificates. Digital certificates exist so you can be extra certain you’re dealing with legitimate entities and not fraudulent ones.
Document Signing

Part of why PKI exists is that you often have multiple parties on the internet that are communicating and interacting with each other. You might not think about it, but each time you go online, you’re likely engaging with various entities and using PKI to do it.
For example, let’s say you go online and want to buy some clothes. Within milliseconds, your device, whether that’s a tablet, laptop, smartphone, etc., will communicate with a website. To ensure there’s mutual trust between the devices, you’ll want to have certificates in place. Without those certificates, there is no reason to trust any website or app’s validity and authenticity.
With PKI, you have one entity electronically signing a document establishing that a specific cryptographic key belongs to an endpoint or specific user. Again, this boils down to authentication, which is part of explicit online trust that has to exist when your device communicates with another device, application, or user.
If you have an enterprise network, you need this functionality. Your system will use a unique cryptographic key to identify an endpoint. That means you have electronic entities that trust one another.
Potential Vulnerabilities
It sounds weird to talk about computers or mechanical entities “trusting” each other. They’re not sentient, but we program them to trust each other based on security protocols we create and implement. There are kinds of protocols like that, with PKI as only one example.
It would be nice to say that if you have a PKI system in place, there is no way for anyone to compromise that trust you’ve built or get around it. Whenever you have a determined hacker, though, they will likely find system vulnerabilities.
PKI is no exception. The main problem is that someone might intercept a secret and strong credential. If they do that, you could say that this hacker has the keys to the castle.
Some individuals in the IT world study this concept, particularly ethical hackers who work to make systems stronger. They say that a little more than four out of five hacking-related incidents utilize stolen or weak credentials.
Still, that’s no reason not to use PKI as part of your daily life. Digital signing with cryptographic keys is still one of the top-shelf security tools that exist today. It’s not impossible for one of the top hackers in the world to get their hands on a credential and exploit it, but it’s not as common as you might think.
Does Your Business Need to Use PKI?

It would be safe to state that the average business needs PKI. You can use it for all kinds of things. For instance, maybe you need your digital signature on some software. If you let anyone in or outside of your company use it, that digital signature identifies it as your proprietary creation.
You need PKI because you can set up restricted VPN or enterprise intranet access with it. You don’t want just anyone using your virtual private network or enterprise intranet. Having PKI in place means you’ll know exactly who uses those resources.
Any time you have workers who use SSL or TLS certificates, they can participate in communications and web browsing experiences and feel much safer about it. None of this would be possible if you did not have PKI in place.
How Do You Set It Up?

Like so many other tasks in the IT field, your IT admin and staff can handle setting up PKI for your business entity. This is a pretty technical process, but some skilled IT staff members should be up to the challenge.
They should know to focus on a few key metrics during this process rather than huge data sets. Tracking your net profit is a simple place to start if you want to implement PKI for your business. If that works well, you might expand the pilot program as time goes on and your company grows.
Now you know some PKI basics. You will probably find that it will work for your business once it is up and running. Your workers should feel more secure, and you’ll know you’re only dealing with reputable entities online.