We have all been under the illusion that the most secured OS in any part of the world is Linux Systemd. This is not the case anymore as a security research made to check how true it is that they are the most secured has shown that what it takes to unravel and crash it is just a single command.
Andrew Ayer, a system administrator has identified a critical bug that has the potential to crash a Linux server that is vulnerable with the use of just a command. He said that after the command is made, it becomes impossible for the system to continue and it cannot be stopped or started again as it will not be able to get signals. Simply put, the server cannot be booted easily.
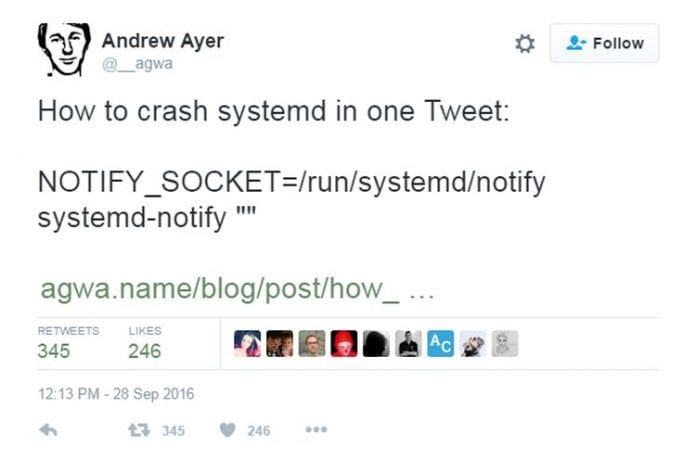
The bug report also mentioned Ubuntu, Debian and CentOS as the being susceptible to different levels of exhaustion resource. The bug in question has been in existence for over two years and will not need root access to succeed.
According to Ayer, if a hacker gets hands on the command in question, PID 1 will hang and remain in the pause system call. This is why you will not be able to stop or start the daemons because of the reasons stated above. He said that this command is very short that it can fit into a Tweet window.
He said that the challenge is how equipped system is to handle such command. He also said that the problem with Systmed runs much deeper than what the bug presents. He concluded that system is defective and will not be difficult for programmers to introduce bugs into it.
Good programmers, he said, know it is quite difficult to write software that will be devoid of bug, which is why they always make programmes as clean as possible to reduce the rate at which bugs can be introduced to them. This is something that developers of systemd are yet to understand and amend.
He said that the company can still do something about this great defect. He said that it is true that many Linux servers make use of systemd especially for the init system, but that this is only because they had to replace a system that was so bad. This, he said, is not applicable to NTP, and DNS network management that it wants to replace. He said that systemd some features that are compelling to replace an existing one, but that there are a lot of risks involved.
He therefore, encouraged system administrators to wait for a system that is more secured than choosing systemd in replacing some services that have been existing. He said that in no distant future, a better alternative will surface, hopefully, there will not be so much harm done from the use of systemd that could disrupt the standards-compliance and modularity.